Malware Defenses
Introduction
Safeguard 10 - Malware Defenses
Malware is any type of software designed to interfere with a device’s normal functioning. It could be a virus, worm, spyware, ransomware, adware, and more. A malware infection can present itself in a number of ways: slowing down the infected device, adding unwanted software to the system, or sending phishing messages to contacts.
Defending against malware is crucial to maintaining networks and endpoints and keeping personal information safe. Fortunately, anti-malware software is easy to maintain and highly effective, when configured appropriately.
Malware Types
Viruses and worms: A virus infects a legitimate program, replicates, and spreads to other computers when activated by a user. A worm acts similarly to a virus but self-replicates and spreads without being activated by a user.
Trojan horses, rootkits, and backdoors: Trojan horses pretend to be legitimate software or hijack legitimate downloads. Rootkits give attackers complete control of a device by attacking the core components of a computer. Backdoors allow attackers to reconnect to an infected device subtly.
Adware, spyware, and keyloggers: Adware prompts the user with unsolicited pop-up advertisements or redirects their browser pages a different site than intended. It’s usually harmless but is often paired with spyware and keyloggers. Spyware monitors your computer’s actions to collect login information, personal information, and browsing habits. Keyloggers are specialized to log everything typed into the computer and send it to an attacker.
Botnets and zombies: Once a computer has been compromised, it can be additionally forced to become a tool for attackers. A botnet is a collection of infected devices that can coordinate attacks against other machines, mine cryptocurrency, and generate spam. If this activity goes unnoticed by the user, the device is often called a zombie.
Ransomware: Ransomware is an increasingly popular type of malware that takes over the system by encrypting its files and demanding a ransom to decrypt them. Typically, ransomware will ask for a cryptocurrency like Bitcoin for payment and specify the amount of time until the files are lost forever. The best defense against a device infected by ransomware is to refuse all demands for payment and maintain regular backups that restore the files.
Procedures
10.1 - Deploy and Maintain Anti-Malware Software
Windows
- Keep your system up to date.
- Use Windows built in malware protection (Windows Defender Antivirus).
- Use a separate anti-malware program. These can be found on the Windows App Store.
Using Windows Defender Antivirus
- Search Windows Security from the Windows Search Bar.
- Select Virus & Threat Protection.
- Here you will see multiple options that will help protect your Windows System.
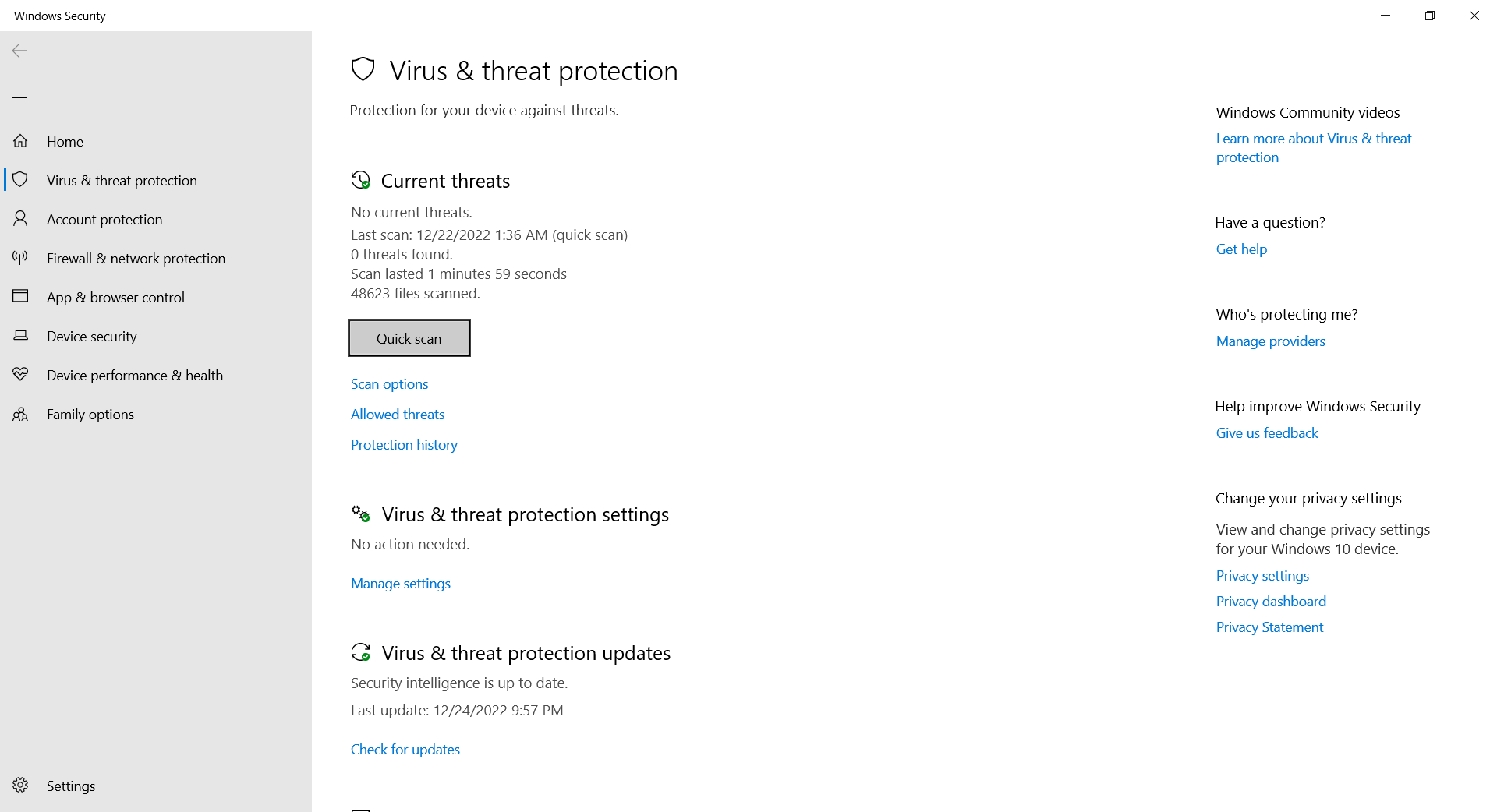
- Current Threats: This option will display any current threats to your system, and allow you to scan your system for more.
- Virus & threat protection settings: This option allows you to change various settings for the antivirus software. Changing these settings is generally not needed for day-to-day use.
- Ransomware Protection: See the guide below on how to use ransomware protection.
How to Use Ransomware Protection
Windows Ransomware Protection involves two main components: Controlled Folder Access and Ransomware Data Recovery. These components can be accessed by going to Windows Security, Virus & Threat Protection Settings, then clicking on Manage ransomware protection under the Ransomware Protection section.
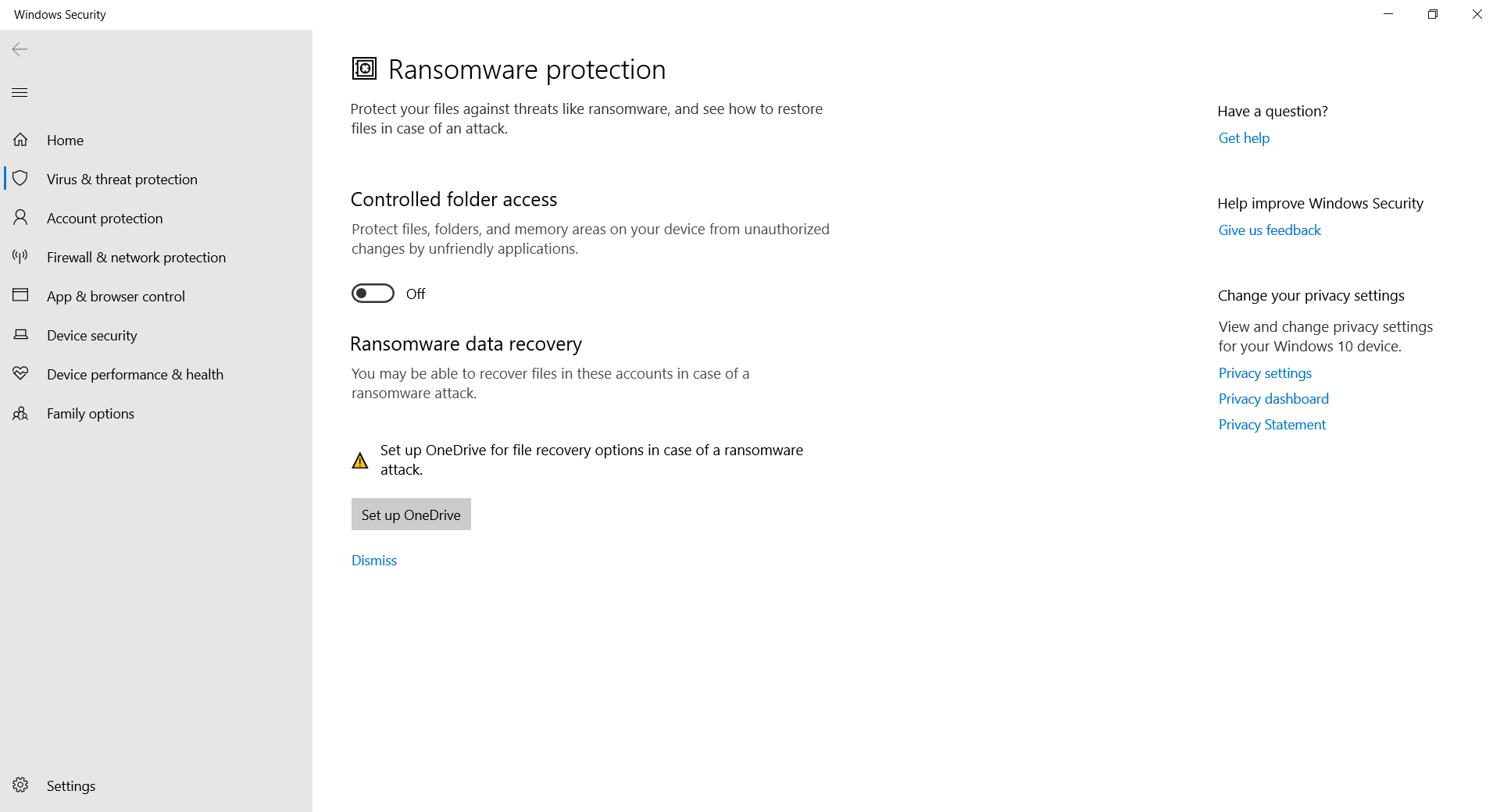
Controlled Folder Access
Controlled Folder Access lets you prevent unauthorized changes to certain files and folders from applications you do not allow.
- To enable, ensure the toggle for Controlled Folder Access is switched on.
- Once enabled, three links should appear below the toggle:
- Block history displays activity on the most recently blocked programs due to Controlled Folder Access
- Protected folders allows you to add or remove files and folders protected by Controlled Folder Access. Windows system folders are protected by default.
- Allow an app through controlled folder access allows you to whitelist an application blocked by Windows.
Ransomware Data Recovery
Ransomware data recovery allows you to back up files onto Microsoft’s OneDrive in case your files become compromised. To utilize this service, click Set up OneDrive if you haven’t already, otherwise click View files to ensure files you want kept safe are present.
Ensure files backed up to OneDrive this way meet the Security And Data Protection policies set by the Division of IT.
macOS
- Keep your system updated.
- Apple describes a three layer defense system on their support website:
- Prevent launch or execution of malware.
- Block malware from running on the system.
- Remediate executed malware.
- Apple systems have three programs designed to carry out these steps: Gatekeeper, Notarization, and XProtect.
Notarization
According to Apple’s support website:
“Notarization is a malware scanning service provided by Apple. Developers who want to distribute apps for macOS outside the App Store submit their apps for scanning as part of the distribution process. Apple scans this software for known malware and, if none is found, issues a Notarization ticket. Typically, developers staple this ticket to their app so Gatekeeper can verify and launch the app, even offline.”
This process ensures software that is on the Apple App store is safe to use on Apple computers and systems. Notarization runs automatically on your Apple system, so configuration is generally not required.
XProtect
XProtect is a built in antivirus software designed to make sure software that may contain malware is not executed on an Apple system. XProtect scans software every time that software is Launched, Changed, or the XProtect systems signatures are updated.
Linux
Linux is generally less prone to malware for the following reasons:
- Software is usually ran as a normal user, which has limited capabilities if configured correctly.
- Most software ran on Linux systems are open source.
- Linux system configurations can be very diverse and different.
Despite this it is still a good idea to keep your Linux system safe through these practices:
- Ensure your system is kept up to date.
- Install programs from official channels wherever possible. Limit program installation from third-party repositories or untrusted channels.
- (Optional) Install antivirus software on your machine.
Ensure Your System is Kept Up to Date
One of the easiest ways to prevent malware from infecting your Linux system is to make sure the system is up to date. Information on how to update your various Linux systems can be found in the Endpoint Patching documentation.
Additionally, it can be beneficial to enable automatic security updates to avoid having to remember to update frequently. Review the following documentation on automatic security updates for:
Install Programs From Official Channels
A common vector for malware on Linux systems is third-party program sources. Thus, it is important that software be installed from package repositories that come by default with Linux distributions. These include:
- Ubuntu: The official Ubuntu repositories
main,restricted,universe, andmultiverse. Software from the Ubuntu Software Center come from official repositories and are therefore also safe. - Debian: The official Debian repositories
stable,main,contrib, andnon-free. - Fedora: The official Fedora repositories
fedoraandupdates.
Packages in the default repositories of each distribution are curated, verified, and vetted by developers of their respective distributions. Packages from third parties should therefore be avoided whenever possible. For the systems listed above, these include:
- Ubuntu: Third party repositories and Personal Package Archives (PPAs).
- Debian: Third party repositories.
- Fedora: Third party repositories.
These sources do not undergo the same process of validation as packages in official repositories. Installation is at the risk of the user. If a piece of software you wish to install cannot be found in the official repositories, some safer alternatives to third party repositories may include:
These two sources provide applications in the form of Flatpacks and Snaps respectively, which are self-contained applications ran in a sandbox. Thus, they have limited access to the host system, reducing the possibility of malware. Additionally, Snap and Snapcraft is developed by Canonical, the company behind Ubuntu.
Packages from Flathub and Snapcraft are not subject to the same scrutiny as packages from official Linux repositories. It is recommended to only install packages from publishers you trust.
Linux Antivirus Software
If you wish to use antivirus software to protect your Linux machine, there are a few recommended programs by distributions:
Ubuntu
- Open source: ClamAV Antivirus, ClamTK.
- Closed source: Avast Core Security, GRAVITYZONE ENTERPRISE SECURITY, ESET NOD32 Antivirus Business Edition for Linux Desktop, XFProt, Sophos Antivirus for Linux, Symantec Endpoint Protection.
Debian
- ClamAV Antivirus - anti-virus utility for Unix - command-line interface.
- ClamTK - A graphical user interface for ClamAV (depends on ClamAV).
- mailscanner - “an e-mail gateway virus scanner and spam detector.”
- amavis-ng - “a mail virus scanner which integrates with different MTA (Exim, Sendmail, Postfix, or Qmail) and supports over 15 virus scanning engines.”
- procmail - " a tool that uses the procmail package, which can scan email attachments for viruses, block attachments based on their filenames, and more."
- exiscan - “an e-mail virus scanner written in Perl that works with Exim.”
- blackhole-qmail - “a spam filter for Qmail with built-in support for Clamav.”
Fedora does not recommend any specific antivirus software, however the software listed above should work on Fedora systems too.
For a basic antivirus that is commonly recommended and easy to use, ClamAV Antivirus works on most Linux distributions. See below for a guide on ClamTK, a GUI frontend to ClamAV Antivirus.
Using ClamTK
ClamTK allows users to easily use ClamAV’s features in a graphical user interface. ClamAV has a variety of useful features to allow users to secure their Linux system.
Installation on Ubuntu (22.04LTS) and Debian
ClamTK can be installed via the command line using the apt-get command:
sudo apt-get install clamtk
Installation on Fedora
ClamTK can be installed via the command line using either dnf or yum.
sudo dnf install clamtk
sudo yum install clamtk
Navigating ClamTK
- Settings: Generally the default settings will be sufficient for day to day use, however you can configure a few aspects of ClamAV such as when to update, and what files to scan.
- Whitelist: The whitelist allows you to prevent ClamAV from scanning them.
- Network: Network allows you to set up a proxy.
- Scheduler: Scheduler allows you to specify when ClamAV will complete it’s scan and when to update its signatures.
- History: History will give you a history of any files it may have found that contain some form of virus or malware.
- Quarantine: This allows you to quarantine any files that may be dangerous.
- Update: Allows you to update the antivirus.
- Update Assistant: Allows you to define how to update your antivirus signatures.
- Scan a file: Have ClamAV scan a file.
- Scan a directory: Have ClamAV scan a directory.
- Analysis: Complete further analysis of files or directories.
Resources
10.2 - Configure Automatic Anti-Malware Signature Updates
Windows
Malware signature updates happen automatically when Windows Update runs. By default, Windows will update automatically during active hours. To view active hours, follow the instructions below for your Windows version:
Windows 11
- Select Start > Settings > Windows Update > Advanced options. Under Active hours, choose to update manually or automatically in Windows 11.
- If you want to adjust your active hours manually, select the start time and end time for active hours.
Windows 10
- Select Start Settings > Update & Security > Windows Update, and then select Change active hours.
- Choose the start time and end time for active hours, and then select Save.
macOS
XProtect, the signature-based anti-malware software on macOS devices, is automatically updated daily by default. Additionally, notarization updates automatically run more frequently than daily.
Linux
To automate security updates in Linux, refer to the respective guide below:
10.3 - Disable Autorun and Autoplay for Removable Media
Windows
- Press Win+R and type
regedit. When prompted, enter administrator credentials to continue. - Navigate to the key
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer. - Look for the entry
NoDriveTypeAutoRun. If it isn’t listed, create a new DWORD value by right-clicking the right pane and selecting New DWORD (32-bit) Value. Name the DWORDNoDriveTypeAutoRun. - Set the value of
NoDriveTypeAutoRuntoFFto disable AutoRun on all drives.
macOS
macOS devices have autorun and autoplay disabled by default.
Linux
The following procedures are organized by environment rather than distribution.
GNOME
To disable for a single user use the following commands:
gsettings set org.gnome.desktop.media-handling automount false
gsettings set org.gnome.desktop.media-handling automount-open false
systemctl restart gdm.service
To disable for all users:
- Create a file
etc/dconf/db/local.d/00-media-automountwith the following:cat /etc/dconf/db/local.d/00-media-automount [org/gnome/desktop/media-handling] automount=false automount-open=false - Apply the changes using the command
dconf update.
Xfce
- Open the Xfce Settings Manager.
- Under Hardware, select Removable Drives and Media.
- Deselect all boxes in each tab: Storage, Multimedia, Cameras, Printers, and Input Devices.
10.4 - Configure Automatic Anti-Malware Scanning of Removable Media
Most security software is capable of automatically scanning removable media for malware. This feature should be enabled whenever possible. The same applies to operating systems.
Windows
All editions of Windows 10 can use the following steps to enable scanning of removable drives during full scans.
- Open PowerShell as administrator.
- Type
Set-MpPreference -DisableRemovableDriveScanning 0into the terminal prompt.
Windows 10 Pro, Enterprise, and Education editions can additionally change the Group Policy to enable this as well.
- Open Run by pressing Win + R.
- Type
gpedit.mscinto Run and click OK. - In the left pane, navigate to Computer Configuration/Administrative Templates/Windows Components/Windows Defender/Scan.
- In the right pane, double-click the Scan removable drives option to edit it.
- Select Enabled and click OK.
Linux
ClamAV is capable of scanning removable drives, but not automatically. However, a custom shell script can be created and set to run whenever a new external drive is mounted via the distribution’s settings.
macOS
Apple devices automatically scan removable drives.
10.5 - Enable Anti-Exploitation Features
Windows
Accessing Exploit Protection Settings
The following settings include Data Execution Protection and Windows Defender Exploit Guard.
- Open the Start menu.
- Type Windows Security and select the Windows Security app from the search results.
- Select App & browser control and then Exploit protection.
Data Execution Prevention
Microsoft Data Execution Prevention (DEP) is a feature that prevents code from executing in specified areas of memory. DEP is enabled by default. In the event that it has been disabled, follow the above instructions to re-enable it.
Windows Defender Exploit Guard
Windows Defender Exploit Guard (WDEG) is a combination of features that make Windows harder to exploit. The components of WDEG are managed by Group Policy, System Center Configuration Manager, and Mobile Device Management such as Microsoft Intune. To configure exploit protection settings, follow the above instructions. Only configure these settings if you know what you are doing.
Apple System Integrity Protection and Gatekeeper
Apple devices has mandatory anti-malware access controls and software that is enabled by default. Both System Integrity Protection and Gatekeeper are enabled by default.
10.6 - Centrally Manage Anti-Malware Software
Departments should centrally manage anti-malware software for their devices and endpoints. By doing this, maintaining security on machines is straightforward as there is a uniform defense, rather than different setups on each device. Regardless of the anti-malware software you use, make sure that it’s deployed on all devices.
Microsoft Anti-Malware for Azure
Microsoft Anti-Malware for Azure is a free software package that can be used for Azure Cloud Services and Virtual Machines. Refer to the official Microsoft documentation for instructions on how to configure and deploy the software.
Microsoft Defender for Endpoint
Virginia Tech’s Microsoft Defender for Endpoint (MDE) service is recommended for endpoint operating systems.
10.7 - Use Behavior-Based Anti-Malware Software
Signature-based security scans for malware signatures, identifiers that are unique for all malware. However, this detection method can only work for known malware. Behavior-based anti-malware software has been developed to detect these novel threats by detecting specific malicious behaviors. Thus, all systems should employ the use of behavior-based anti-malware software in addition to signature-based anti-malware.
Microsoft Defender for Endpoint
Virginia Tech’s Microsoft Defender for Endpoint (MDE) service is recommended for endpoint operating systems.
Other
If you have questions that are not covered in these procedures, please contact the VT IT Security Office itso@vt.edu for a consultation.


