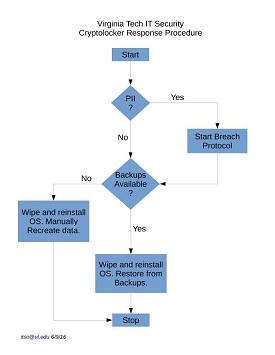
If you encounter a Ransomware or Cryptolocker attack, report the Incident to the ITSO.
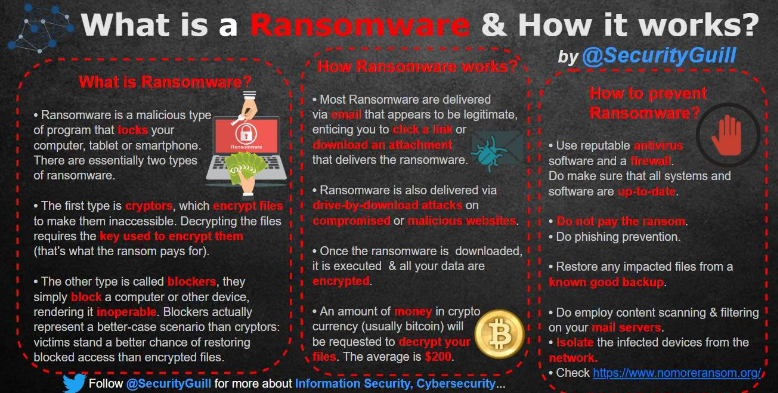
Periodically, VT faculty and staff receive phishing email messages with subject lines such as “Missing payments for invoices.” These emails contain malicious attachments that encrypt local system files as well as files on shared network drives. After the files have been encrypted, users are then prompted to purchase a password from cyber-criminals in order to decrypt them.
Here are some general steps you can take to limit the disruption caused by a ransomware attack.
- Do a HIGH-risk data inventory. Find where you store this data. Know who can access your file shares. Attackers threaten to disclose your sensitive data unless a ransom is paid. There is NO guarantee they will not disclose information after payment. Once you find high-risk data on your computer, you need to encrypt it at rest or in transit per the Virginia Tech Minimum Security Standard. Windows 10 has a built-in ransomware protection feature that needs to be enabled. This feature is currently only available for Windows 10.
- Backups: This is the most critical step in your ransomware recovery process. Be sure you have good backups that can be restored quickly. Test your backup restoration once or twice a year. The backups should be isolated (air-gapped) from your systems and network in order to prevent ransomware from encrypting your backup files. Ensure your recent backups are offline from the users.
- Least Privilege: Ensuring users only have access to the files they need and have no extra permissions is a really difficult and time consuming process but it will limit the extent and damage caused by ransomware. For example, the Accounting Department should only have read/write on the Accounting share of a file server. If they have read/write to other folders (HR, marketing, etc.) and an accountant gets hit with ransomware, then all extra data that the accountant could access but didn’t need may get encrypted. Limit access to only the files and folders each user needs to do their job.
- Encryption: Per our standards, the only time high-risk data should be in the clear is when it’s in use. In the event of a ransomware attack, if high-risk files are encrypted at rest, then the attackers get an encrypted file which hopefully renders their ransom demands useless. They’re left with wiping the files on your systems out as their only recourse. Hopefully, good backup strategies address that event.
- Access Control, Logging and Visibility: In today’s WFH world, RDP and other remote access services are targeted by attackers to gain access to internal systems. Ensure all local account passwords follow VT’s password strength rules. Make sure your logs will help you answer the following questions:
- When were high-risk files accessed? Was it successful?
- Who accessed them?
- What did they do with the files (delete, copy, move)?
- How did they access the files?
- Training/Awareness: Ensure your users are aware they are potential targets of ransomware attacks because of the data they use in their job. The Information Technology Security Office is committed to presenting technology security awareness sessions to anyone associated with Virginia Tech. If your area is interested in learning more about this educational opportunity, please complete the Awareness Training form in ServiceNow.
Technical Information
- Configure computers to use the ITSO’s Secure DNS. These DNS resolvers obtain ransomware feeds daily and will block network connections to known cryptolocker hosts. For more information, please see: https://dns-block.iso.vt.edu/
- Deploy granular file system and share permissions on network file shares. This isolates and limits the damage to only certain file paths. For example, employees in ‘Accounting’ typically should not have access to ‘Marketing’ files or ‘Academic’ files located in the same share.
Ransomware and cryptolockers are on the rise. If you fall victim, follow our cryptolocker incident response diagram and report any and all potential PII data disclosures to the IT Security Office. Also, be aware that some forms of ransomware can be decrypted and several antivirus companies offer free decryption tools.
Also, be aware that some forms of ransomware can be decrypted and several antivirus companies offer free decryption tools
https://www.avg.com/ww-en/ransomware-decryption-tools
https://noransom.kaspersky.com/
https://www.mcafee.com/us/downloads/free-tools/shadedecrypt.aspx
https://www.thewindowsclub.com/list-ransomware-decryptor-tools
Finally, if you are unable to recover your files, please do not pay the ransom. Contact the ITSO for further guidance.
References:
Ransomware information/guidance
https://www.cisa.gov/stopransomware
https://csrc.nist.gov/projects/ransomware-protection-and-response
Working from Home Security
https://www.cisecurity.org/blog/5-network-security-remedies-for-telework/