Incident Response Management
Introduction
Safeguard 17 - Incident Response Management
A cyber security incident is defined by the Department of Homeland Security as:
An occurrence that (1) actually or imminently jeopardizes, without lawful authority, the integrity, confidentiality, or availability of information or an information system; or (2) constitutes a violation or imminent threat of violation of law, security policies, security procedures, or acceptable use policies.
Source: OMB M-17-12
Information Technology (IT) is responsible for:
- Maintaining an incident response procedure document.
- Maintaining the Computer Incident Response Team (CIRT) to carry out these procedures.
- Arranging for intake of reports of suspected IT security exposures of university data and other suspected cyber incidents.
There are six main steps of the VT Cyber Incident Response Plan.
- Preparation: Maintaining and improving incident response capabilities; preventing incidents by ensuring that systems, networks, and applications are sufficiently secure.
- Identification, Detection, and Analysis: Confirming, characterizing, classifying, categorizing, scoping, and prioritizing suspected incidents.
- Containment: Minimizing loss, theft of information, or service disruption.
- Eradication: Eliminating the threat.
- Recovery: Restoring computing services quickly and securely. Assessing response to better handle future incidents through utilization of reports, “Lessons Learned,” and after-action activities, or mitigation of exploited weaknesses to prevent similar incidents from occurring in the future.
- Incident Closure: Closing the incident and monitoring affected devices for future incidents, if applicable.
Preparation
Preparation is the most important part of any incident response plan. It focuses on being proactive rather than reactive, which prevents incidents from occurring in the first place. It consists of every step taken to ensure systems are up to date and sufficiently secured.
The phase is important because it maintains compliance and increases communication. This ensures that organizations are not penalized or fined for not meeting compliance standards. It also increases communication by establishing a communication plan, which minimizes confusion and misunderstandings.
The preparation phase has several key elements:
- Incident Response Plan: A plan to outline the procedures for detecting, identifying, and resolving security incidents. It identifies important assets, defines incident types, creates response protocols, defines the incident response team’s roles and responsibilities, and establishes a communications plan. The plan should be regularly evaluated and improved as needed.
- Incident Response Team (IRT): A team of officials from essential departments such as IT, security, legal, and communications. Each member should have clearly defined responsibilities and training to handle various types of security scenarios.
- Training and Awareness: Awareness programs and security trainings help everyone to know what to do to prevent or act during an incident.
- Security Controls: Methods used to increase security, such as firewalls, intrusion detection, access controls, and prevention systems.
Identification, Detection, and Analysis
The identification, detection, and analysis phase is the first step of incident response. It is crucial in order to minimize the effects of security incidents.
- Determine where the incident originated from, if it truly occurred.
- Respond to the incident and minimize its impact.
- Gather and preserve evidence.
- Analyze the issue to determine the best way to remediate the problem.
Containment
Containment limits the scope and magnitude of a security incident by gathering, securing, and documenting all evidence. This is done by preventing data from leaving the network via affected devices and preventing the attacker from causing further damage to Virginia Tech IT assets.
By isolating the danger in an incident, the damage is minimized, preventing the incident from becoming more serious and protecting vital assets. Containment also preserves evidence and gives the incident response team time to analyze the situation and create a response plan.
Containment uses several different strategies to work efficiently:
- Non-technical Controls: Useful strategies such as physical security measures, rules, access controls, password guidelines, and security awareness training.
- Technical Controls: Controls such as firewalls, intrusion detection systems, and antivirus software.
- Communication Strategy: A plan to establish clear communication and make sure all involved parties stay informed.
- Testing and Validation: Methods to make sure that the threat has been properly eliminated, such as running scans, evaluating backups, and watching the network for evidence of compromise.
- Use technical and non-technical controls to isolate the incident.
- Establish a communication plan to to establish clear communication and make sure all involved parties stay informed. Refer to Appendix G of the incident response guidelines for a communications tracking worksheet.
- Conduct testing and validation.
Eradication
Eradication involves the removal of malicious code, accounts, or inappropriate access and the repair of any vulnerabilities that may have been the root cause. It’s crucial to remove every component of the threat, including hidden files and registry entries.
- Implement the eradication plan using relevant technical and manual methods, such as running antivirus scans, restoring system backups, or manually removing malicious files or software. Prioritize critical systems.
- Test and confirm that the threat has been entirely eliminated before returning the machine to normal operation.
- Update documentation from the lessons learned.
- Evaluate and review the process to find areas that can be improved.
Recovery
Recovery restores all affected devices and data after removing the threat. Once systems and data has been restored, the incident response team has a post-incident review to assess the effectiveness of the incident response plan and make improvements as needed.
- Prioritize recovery efforts based on the status of the affected systems and data.
- Restore impacted systems and data by following the recovery plan.
- Validate the recovery of all affected systems.
- Communicate with stakeholders to keep them informed about the incident status and recovery efforts.
- Once the incident has been fully resolved, document lessons learned from the incident in a post-incident review.
Incident Closure
Incident closure makes sure that all incident-related tasks are completed so that the company and its affected devices can resume regular operations.
- Confirm that all incident-related tasks are finished.
- Verify that the incident has been thoroughly addressed and resolved.
- Conduct a post-incident analysis of the incident response process to evaluate effectiveness. Identify any residual risks or vulnerabilities.
- Communicate as necessary with stakeholders and address any concerns they may have.
- Update the incident response plan with lessons learned, improvements, and recommendations.
- Resume regular operations.
Procedures
17.1 - Designate Personnel to Manage Incident Handling
University Authorities are those who make requests and decisions regarding cyber security incident response at Virginia Tech, including whether or not to activate the Cyber Incident Response Team (CIRT). For more information about University Authorities and their roles, see Procedure 17.5.
CIRT Organization
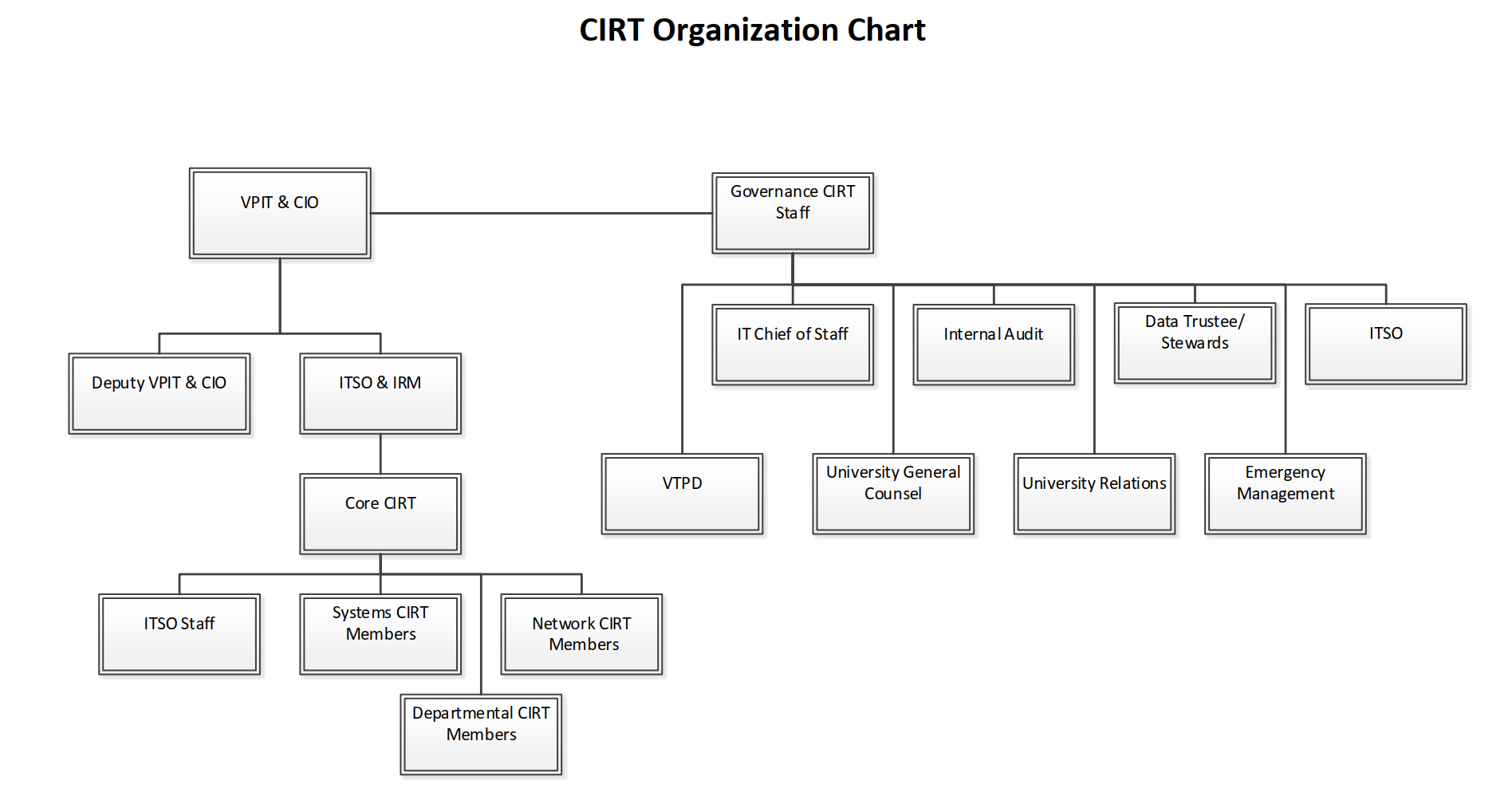
Incidents are handled by the VT-CIRT, which is comprised of people from the IT Security Office and Division of Information Technology:
- Secure Identity Services (SIS)
- Network Infrastructure and Services (NI&S)
- IT Experience & Engagement AKA 4Help
- Enterprise Systems
- Advanced Research Computing (ARC)
- Collaborative Computing Services (CCS)
- University college and departmental representatives of the IT Council
- University Compliance Officers
17.2 - Establish and Maintain Contact Information for Reporting Security Incidents
Refer to Appendices C, D, H, and K of the incident response guidelines for internal and external contact information.
17.3 - Establish and Maintain an Enterprise Process for Reporting Incidents
IMPORTANT: If an incident is illegal or life threatening, contact the Virginia Tech Police: 540-231-6411 or Emergency: 911.
If you believe a server, application, or account has been hacked, you may report the incident in 4Help. The IT Security Office can also be reached via itso-g@vt.edu or 540-231-6020.
When in doubt, report it.
Report events that have an impact on your organization. Reportable incidents include but are not limited to:
- Damage is done.
- Loss occurs.
- Malicious code is implanted.
- There is evidence of tampering with data.
- Unauthorized access has been gained or repeated attempts at unauthorized access have been made. This can be from internal or external sources.
- There has been a threat or harassment via an electronic medium (internal or external).
- Access is achieved by the intruder.
- Web pages are defaced.
- A user detects something noteworthy or unusual (a new traffic pattern, new type of malicious code, a specific IP as the source of persistent attacks).
- There is a denial of service attack on the agency.
- Virus attacks adversely affect servers or multiple workstations.
- Other information technology security incidents occur that could undermine confidence and trust in the Commonwealth’s Information Technology systems.
- Login to 4Help.
- Go to the Have I been hacked? knowledge base (KB) article.
- Follow the General Incident Guidelines.
- Keep the system powered on.
- Unplug any network cables and disable wireless. This disconnects it from the Internet while preserving evidence.
- If you’ve been locked out of your Virginia Tech account, contact 4Help to restore access.
- Only tell people who need to know about the issue in order to maintain confidentiality.
- Click Request this service.
- Fill out the reporting form and click Submit.
17.4 - Establish and Maintain an Incident Response Process
The incident response guidelines are detailed on the IT Security Office website. A summary of the major steps is provided below.
- Determine if the incident occurred.
- Analyze the precursors and indicators.
- Look for correlating information.
- Perform research by consulting search engines, knowledge base, etc.
- Once the handler believes an incident has occurred, begin documenting the investigation and gathering evidence.
- Prioritize handing of the incident based on the relevant factors (e.g. functional impact, information impact, recoverability effort, etc.).
- Report the incident to the appropriate internal personnel and external organizations. Refer to Appendices C, D, H, and K of the incident response guidelines for internal and external contact information.
- Acquire, preserve, secure, and document evidence.
- Contain the incident.
- Eradicate the incident.
- Identify and mitigate all vulnerabilities that were exploited.
- Remove malware, inappropriate materials, and other similar components.
- If more affected hosts are discovered (e.g. new malware infections), repeat steps 1A and 1B to identify all other affected hosts, then contain (5) and eradicate (6) the incident again.
- Recover from the incident.
- Return affected systems to an operationally ready state.
- Confirm that the affected systems are functioning normally.
- If necessary, implement additional monitoring to look for future related activity.
- Create a follow-up report.
- Hold a lessons learned meeting. This is mandatory for major incidents, optional otherwise.
17.5 - Assign Key Roles and Responsibilities
IT Security Office
The Vice President for Information Technology and CIO has given the Virginia Tech IT Security Office (ITSO) full authority to act in a manner to protect the integrity, confidentiality, and availability of Virginia Tech’s information technology infrastructure.
The ITSO manages and coordinates detection, identification, containment, eradication, and recovery efforts of reported cybesecurity incidents with Virginia Tech departments’ IT personnel. The IT Security Officer also has the authority to classify threats as a risk to the enterprise and can activate the VT-CIRT team at his discretion.
University Authorities
University Authorities are those authorized to make requests and decisions regarding cyber security incident response at Virginia Tech.
| University Authority | Role |
|---|---|
| Vice President for Information Technology and Chief Information Officer (CIO) | Respond to IT security incidents by BOV Resolution. |
| Information Technology Security Officer (ITSO) | Delegated authority by CIO to decide whether to activate CIRT; notifies Incident Governance Team of decision. |
| VT CIRT Governance Team | A broad range of university stakeholders (see Appendix A of the incident response guidelines). |
| University Legal Counsel | Oversee any law enforcement/legal actions, questions about information disclosure, and legal aspects of the investigation. |
| University President | Manage personnel actions for staff. |
| Executive Vice President and Provost | Manage personnel actions for faculty. |
| University Internal Audit | Ensure data integrity of critical University data, compliance with University procedures and fraud investigations. |
| Division of Student Affairs/Student Conduct | Oversee offenses by Virginia Tech students. |
| Data Trustees/Stewards | Manage sensitive or non-public data access and governance. A list of data trustees and stewards is at https://it.vt.edu/resources/policies/adms.html. |
VT Cyber Incident Response Team (VT-CIRT)
The CIRT Team will only be activated if a cyber security incident has been identified as affecting University IT systems/services at an enterprise or a multi-departmental level.
Responsibilities
- Protect the well-being of the University community.
- Protect the confidentiality, integrity, and availability of University systems, networks and data.
- To help University personnel recover their business processes after computer or network security incidents.
- To provide a consistent response strategy to system and network threats that put Virginia Tech data and systems at risk.
- To develop and activate a communications plan including initial reporting of the incident as well as ongoing communications as necessary.
- To address cyber related legal issues.
- To coordinate efforts with external Computer Incident Response Teams.
- To minimize the University’s reputation risk by notifying appropriate University officials of cyber incidents that may become high profile events and implementing timely and appropriate corrective actions.
Roles
- Vice President for Information Technology and CIO
- Information Technology Security Officer
- University Legal Counsel
- University Internal Audit
- VT Police Department
- Data Trustees/Stewards
- University Relations
More information regarding key roles and responsibilities for incident response management are defined in the Virginia Tech incident response guidelines.
17.6 - Define Mechanisms for Communicating During Incident Response
University Relations, Information Technology, and the appropriate stakeholders must develop a communications plan whenever a breach of Personally Identifiable Information (PII) has been confirmed. A communications diagram for PII exposure is provided in Appendix B of the incident response guidelines.
Communications during incident response is guided by the communications plan. A good communications plan minimizes confusion, increases responsiveness, and focuses efforts by doing the following:
- Identify the stakeholders and those authorized to speak about the incident.
- Establish communication channels for internal and external stakeholders.
- Create a communication schedule, including the planned frequency of communications among internal and external stakeholders, respectively. Refer to Appendix G of the incident response guidelines for a communications tracking worksheet.
- Establish procedures for notifying external organizations directly involved with the incident.
- Share action plans.
- Establish means of keeping University stakeholders updated on the incident.
17.7 - Conduct Routine Incident Response Exercises
Practicing incident response allows for the incident response team to identify possible issues with the incident response plan and proactively improve it. Conducting routine incident response exercises increases team communication and prevents mistakes, miscommunication, and confusion during actual security incidents.
As part of incident response preparations, university colleges and departments have an annual IT risk assessment (ITRA) and participate in an annual tabletop exercise using the incident response guide.
17.8 - Conduct Post-Incident Interviews
Post-incident interviews take place as the lessons learned meeting, which is mandatory for all major incidents. The meeting should analyze the incident response process and address any areas that need improvement.
- Confirm that all incident-related tasks are finished.
- Verify that the incident has been thoroughly addressed and resolved.
- Conduct a post-incident analysis of the incident response process to evaluate effectiveness. Identify any residual risks or vulnerabilities.
- Communicate as necessary with stakeholders and address any concerns they may have.
- Update the incident response plan with lessons learned, improvements, and recommendations.
- Resume regular operations.
Other
If you have questions that are not covered in these procedures, please contact the VT IT Security Office itso@vt.edu for a consultation.




